MONITORAPP Web Application Firewall (AIWAF)
AIWAF guarantee safety without any service latency, using high proxy technology.
What’s MONITORAPP
KNOW MORE ABOUT MONITORAPP
AIWAF (Application Insight Web Application Firewall) is a Web Application Firewall product that provides Website security for in-bound traffic and protects Website from hacking and it is configured as PROXY in the network, with patent technologies within the WAF solution. AIWAF guarantee safety without any service latency, using high proxy technology.
AIWAF Features
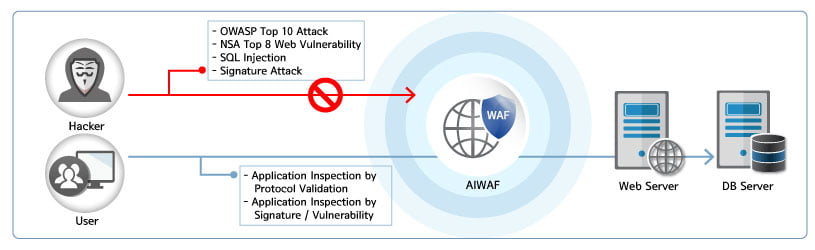
Blocking various patterns of web attack
- OWASP Top 10
- XSS / Injection Attack Block
- HTTP based DDOS Attack Block
- Application Exploits Block
- SSL Termination
- Latest Web Vulnerability Attack Block via Automated Updated Function
- Bot detection
- Redirect Encoding Attack
- Forceful browsing
- Worm / Virus / Malware Detection
- Buffer-Overflow
- Cookie Forgery
- Crawling / Scraping
- Web Shell
AIWAF Benefits
AIWAF Strengths
Intuitive and User-friendly interface based on WEB
Various log search & easy management
Interworking with integrated log via SNMP, SIEM
Statistics & Report
Protection for Personal Information Leakage (Masking)
Blocks Uploading/Downloading the File which Contains Personal Information
Intuitive and User-friendly interface based on WEB
Various log search & easy management
Interworking with integrated log via SNMP, SIEM
Statistics & Report
Protection for Personal Information Leakage (Masking)
Blocks Uploading/Downloading the File which Contains Personal Information
AIWAF Models
AIWAF Models
| Specification | AIWAF-200_Y20 | AIWAF-500_Y17 | AIWAF-1000_Y17 | AIWAF-2000_Y17 | AIWAF-4000_Y17 AIWAF-8000_Y18 |
|---|---|---|---|---|---|
| Appearance |  |
 |
 |
 |
 |
| RAM | 8GB (Max 32GB) | 16GB (Max 64GB) | 16GB (Max 64GB) | 32GB (Max 256GB) | 32GB (Max 256GB) |
| HDD | 500G | 500G | 2TB | 2TB | 4TB |
| NIC (Default) | 1G UTP * 4 | 1G UTP * 6 | 1G UTP * 2 1G UTP *4 or 1G Fiber *4 or 10G Fiber *2 |
10/100/1000 * 2 1G UTP *4 or 1G Fiber *4 or 10G Fiber * 2 |
10/100/1000 * 2 1G UTP *4 or 1G Fiber *4 or 10G Fiber * 2 |
| NIC (Option) | NIC Slot count 1 Support NIC Type – 1G UTP 4Port – 1G Fiber 4Port – 10G Fiber 2Port |
1G UTP * 4 * 2 or 1G Fiber * 4 * 2 |
1G UTP * 4 * 3 or 1G Fiber * 4 * 3 or 10G Fiber * 2 *3 |
1G UTP * 4 * 7 or 1G Fiber * 4 *7 or 10G Fiber * 2 |
1G UTP * 4 * 7 or 1G Fiber * 4 *7 or 10G Fiber * 2 * 7 |
| Size | 438(W) * 44(H) * 420(D) | 438(W) * 88(H) * 450(D) | 440(W) * 88(H) * 600(D) | 440(W) * 88(H) * 600(D) | 440(W) * 88(H) * 600(D) |
| Power supply | 300W Single | 300W Redundant | 860W Redundant | 860W Redundant | 860W Redundant |
AIWAF Patented Technologies
Transparent Proxy
APPLICATION INSIGHT WAF is operated in Stealth-mode without IP address.
- No environmental change to the pre-existing network
Adaptive Profiling Technology
APPLICATION INSIGHT WAF is operated in Stealth-mode without IP address.
- No environmental change to the pre-existing network
Intelligent User Tracking
- Detects and blocks the actual access IP by learning the association between detected logs from APPLICATION INSIGHT WAF and APPLICATION INSIGHT DFW.
- MONITORAPP’s own patented technology which can find the actual IP that accesses DB through the interworking function.
AIWAF has excellent Performance
- High-performance packet processing and high-traffic processing through load balancing algorithm.
- The largest number of customers based on 10G web application firewall.
- Complete web attack protection through multiple defense modules and simultaneous automatic learning policies based on request and response provision.
- Features of Fail-over and Fail-open in order to provide non-stop web services.
- Provides reliable HTTPS processing performance based on H / W SSL acceleration card. (Reference that handles HTTPS 3G traffic).
- Ensure web service availability through auto bypass (optional) when web service interruption occurs due to performance limit.
Why AIWAF
Why You Choose AIWAF
IT Compliance
- Amendment of Personal Information Protection Law – Establishment of system with security intrusion prevention and intrusion detection function to prevent unauthorized access and infringement by information network.
- Applying HIPAA (US Medical Record Retention Criteria).
- PCI-DS (Payment Card Industry-Data Security Standard) – Card merchants, service providers, credit card payment agency (VAN) should be certified by meeting all the 12 standards of PCI-DSS.
Web Security
- 80 port is vulnerable to hacking due to open web service.
- Danger of data leakage via DB access when web application is hacked.
- Increase of web attack threat due to limitation of existing security products like IDS and IPS.
- Increase of data access route via web by communication development such as mobile phone and SNS.
