
Simulation of IT infrastructure for cyberattack detection
Defensys Threat Deception Platform is a comprehensive all-in-one tool for digital infrastructure simulation designed to proactively detect and prevent cyberattacks. With a complex combination of lures and traps, Defensys TDP detects intruders, delays their progress within the network, and ensures cyberattack mitigation.
Key benefits
- Detects attacks that other tools fail to detect (targeted attacks, zero-day threats, and more).
- Reduces the intruders’ progression within the network by creating an additional emulated elements layer.
- Helps to prevent attacks earlier to limit the impact of a threat.
- Identifies security vulnerabilities to understand intruders’ tools and behaviour against the company’s infrastructure.
How does it work?
Using a combination of traps and lures, Defensys TDP detects the presence of a cybercriminal or malware, delays its progress within the network by confusing it with fake objects, and enables cybersecurity specialists to stop the development of an attack before it leads to significant damage. Traps are hosted on separate Trap Manager servers, while the platform and the entire emulated infrastructure are managed on the Control Center server. The Control Center server is the place where security events are collected and processed, interaction with external systems is provided, and traps, lures and Trap Manager servers are managed. For large organization infrastructures, the scaling task is easily solved by adding the required number of Trap Manager servers.
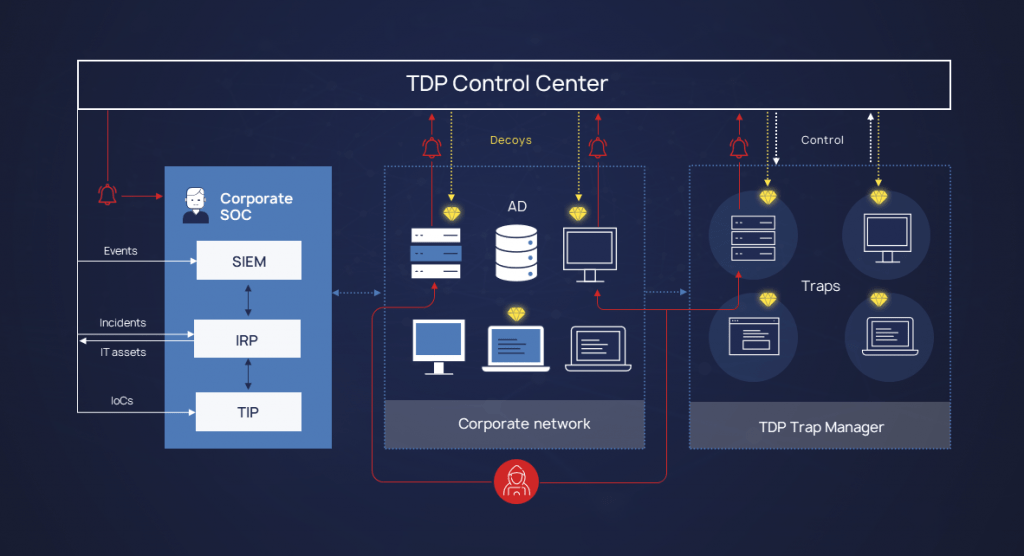
Defensys tdp
System Benefits
- Flexible traps and lures configuration to better adapt and respond to changing company’s real infrastructure dynamics
- Maze-like tools to lure attackers by mimicking a live system with all the typical users and services activity
- High deployment and scalability through the automatic deployment of traps and lures
- Clear detection of compromised systems and automated response when deployed with other Defensys products
Automatic deployment of traps
The Defensys TDP platform allows you to automatically deploy traps that simulate an organization’s real IT assets and manage them from a single centre. A trap represents a resource of interest to an attacker. Defensys TDP allows you to create traps of various types that recreate a wide range of systems in an organization’s infrastructure, such as:
- Windows/Linux virtual machines
- Virtual appliances, networking devices, industrial controllers
- Basic emulation: SSH, HTTP(s), FTP, Telnet, POP3, IMAP, SMTP, SOCKS5, VNC, RDP, PostgreSQL, MySQL
To make the traps alluring and more believable, they are combined into groups of interacting hosts, services, or applications that work together to mimic a computer network.
Lure generation and placement
To attract an intruder’s attention, lures are automatically placed on nodes of the real infrastructure. The lure represents information that holds value to the attacker who has penetrated the network. Such information can be:
- Configuration files of popular administration tools
- Data files (Word / Excel / PDF)
- User accounts
- Browsing history
- SSH keys
- Credentials for connecting to the DBMS
Incident notification and response
Traps and lures are designed solely to attract the attention of an intruder and are not used in regular work processes, so any interaction with them is highly likely to indicate an incident.
Defensys TDP collects events when logging interaction with lures and traps, processes them and sends a detection alert to the cybersecurity expert.
The platform can also send events and necessary context to external systems such as SOAR, SIEM, and TIP to respond and prevent the development of an attack.
Integration with Defensys products
To create the most realistic traps and lures possible, Defensys TDP allows you to use asset data from Defensys SOAR or Defensys SGRC systems. The Defensys TDP platform detects the interaction of both external and internal intruders with traps and sends alerts to cybersecurity specialists.
Events can be sent to the Defensys SENSE system for investigation, which will automatically create timelines reflecting trap interactions, providing the necessary context to the SOC analyst. The received incidents can be transferred to Defensys SOAR so that the playbooks can be used to automate the response process.
Attributes and indicators of compromise collected by Defensys TDP can be automatically sent to the Defensys Threat Intelligence Platform (TIP). The Defensys TIP, in return, will enrich this data, identify correlations with other available TI data, configure automatic monitoring in SIEM events, and export indicators of compromise to cybersecurity tools for blocking.
