Now, protect web applications with AIWAF.
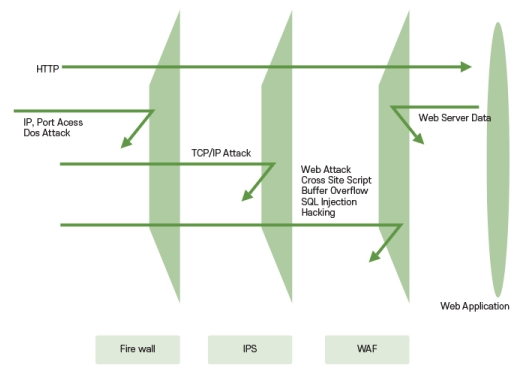
The web is vulnerable. Because the HTTP/HTTPS ports must always be open to show the Web to clients, various attacks can be introduced through them. MONITORAPP’s web application firewall, AIWAF is specialized for traffic-based detection of hacking attempts using vulnerabilities in the Web and for controlling access to servers. Web attacks are evolving every day, causing malicious traffic or falsifying request information. Only WAF that does not stop ongoing development to respond to new types of web attacks can do the right thing. The answer is AIWAF in MONITORAPP.
Defends fully any attack through the web.

Typical web attacks being defended by AIWAF
- – Malware Infection Detection
- – SQL Injection
- – XSS/CSRF
- – Vulnerable Page Access
- – Buffer-Overflow
- – Malicious File Access
- – Scanner/Proxy/Spambot Detection
- – Encoding
- – Upload Malicious File Access
- – Command Injection
- – Cookies falsified
- – Header Vulnerability
- – File system Access
- – Web Server/Application Vulnerability
- – Worm/Virus
- – Directory Access

Enjoy the best performance without slowing down your web services
AIWAF’s transparent proxy technology is implemented as a proxy type without changing the existing network configuration. High-performance packet processing and load balancing algorithms maximize the performance of high-capacity traffic. It has SSL traffic handling, but it automatically scans non HTTP traffic, bypasses, and accelerates through Web caching to ensure maximum performance without sacrificing speed. Fail-open and fail-over features for non-disruptive delivery of Web services, and automatic by-pass function ensure web service availability in the event of a web service failure due to performance limits.
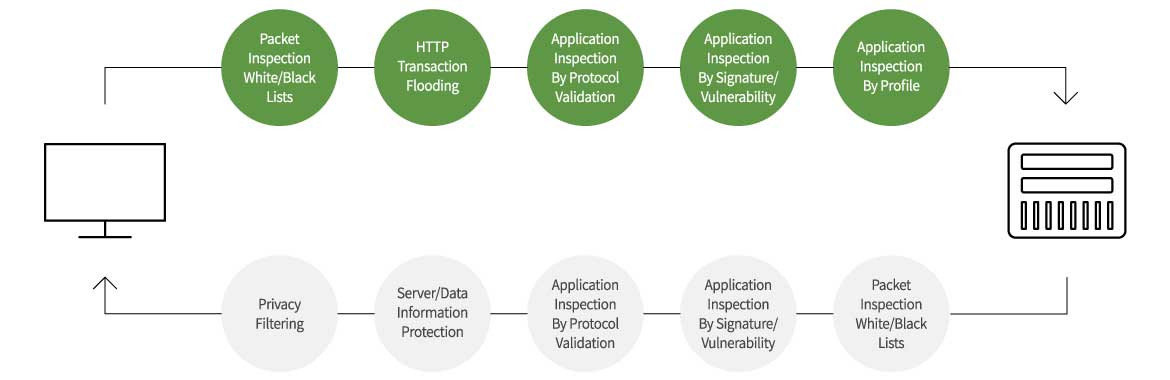 ▲AIWAF function process flow
▲AIWAF function process flowProvides intuitive UI and detailed dashboards.
AIWAF UI is designed to be intuitive and easy to manage for security personnel. User satisfaction is maximized with a convenient interface, intuitive controls, visible reports of attacks and traffic, and monitoring of web server service health.
More convenient.
Over 14 years focusing on WAF
AIWAF has already been recognized for its performance as it has been supplied to more than 4,000 public institutions and financial institutions at home and abroad. BMT has proven performance that surpasses domestic and foreign competitors, and it is being supplied to the first financial group, the virtual currency exchange, and large public institutions to expand its global customer base.




